MOSQUITO attack allows to data extrusion from Air-Gapped computers via leverage connected speakers
MOSQUITO is new technique devised by a team of researchers at Israel’s Ben Gurion University, led by the expert Mordechai Guri, to exfiltrate data from an air-gapped network computers using speakers, headphones, earphones, or earbuds.MOSQUITO: Covert Ultrasonic Transmissions between Two Air-Gapped Computers using Speaker-to-Speaker Communication
The attack is only experimental at this point, has not been seen in the
real world, but has been proven to work and researchers have also created a
custom protocol for transmitting data between two computers —one
air-gapped and one Internet-connected that can relay the data further.
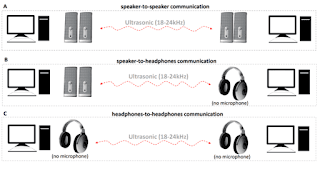
Attack scenarios include speaker-to-speaker exfiltration,
speaker-to-headphones, and headphones-to-headphones.
Jack retasking strikes again!
The attack —nicknamed MOSQUITO— is possible because of a technique
called "jack retasking" that reverses output audio jacks to input
jacks, effectively turning speakers into (unconventional) microphones.
The same research team explored jack retasking in a previous research
project last year, called Speake(a)r, which researchers used to turn headphones into
microphones and record nearby audio and conversations.
For the current experiment, researchers argue that malware that managed
to infect an air-gapped computer can transform and modulate locally stored
files into audio signals and relay them to another nearby computer via
connected speakers, headphones, earphones, or earbuds.
The receiving computer, also infected with malware, uses jack retasking
to convert connected speakers, headphones, earphones, or earbuds into a
makeshift microphone, receive the modulated audio, and convert back into a data
file.
MOSQUITO attack supports pretty fast transfer speeds
Researchers created a custom data protocol that modulates binary data
into audio signals, and they tested their attack for distances between 1 and 9
meters (3.2 to 29.5 feet).
Researchers said they managed to transfer data between two computers with
speeds varying from 1800 bits/s and 1200 bits/s for speakers facing each other
and emitting sound in audible frequency bands (lower than 18kHz).
Transfer speeds decreased if the speakers weren't facing each other, the
distance between speakers increased, or audio frequency changed (towards low or
high frequency). While the first two factors are self-explanatory, the last
needs an additional explanation.
"The reason for that is that loudspeakers, and particularly home
grade PC loudspeakers, were projected and optimized for human auditory
characteristics, and therefore they are more responsive to the audible
frequency ranges," said researchers.
Transfer speeds also decreased when using earphones or earbuds (varied
between 600 bits/s and 300 bits/s) and went even lower for headphones (around
250 bits/s). The reason was that headphones directed their sound waves in one
particular direction, limiting efficient exfiltration cases to very small
distances when headphones were close to each other, and when they emitted sound
in audible frequencies only.
Other factors that decreased data transfer speeds included environment
noise such as music and speech, but researchers said this could be mitigated by
moving the data exfiltration frequency above 18kHz.
The research team discusses various mitigation and countermeasures in
their research paper entitled "MOSQUITO: Covert Ultrasonic Transmissions
between Two Air-Gapped Computers using Speaker-to-SpeakerCommunication."
They also released the following demos to showcase their work.
The research center from the Ben-Gurion University of the Negev who came
up with this new data exfiltration technique has a long history of innovative
and sometimes weird hacks, all listed below:
LED-it-Go - exfiltrate data from air-gapped systems via
an HDD's activity LED
SPEAKE(a)R - use headphones to record audio and spy on nearby users
9-1-1 DDoS - launch DDoS attacks that can cripple a US state's 911 emergency systems
USBee - make a USB connector's data bus give out electromagnetic emissions that can be used to exfiltrate data
AirHopper - use the local GPU card to emit electromagnetic signals to a nearby mobile phone, also used to steal data
Fansmitter - steal data from air-gapped PCs using sounds emanated by a computer's GPU fan
DiskFiltration - use controlled read/write HDD operations to steal data via sound waves
BitWhisper - exfiltrate data from non-networked computers using heat emanations
SPEAKE(a)R - use headphones to record audio and spy on nearby users
9-1-1 DDoS - launch DDoS attacks that can cripple a US state's 911 emergency systems
USBee - make a USB connector's data bus give out electromagnetic emissions that can be used to exfiltrate data
AirHopper - use the local GPU card to emit electromagnetic signals to a nearby mobile phone, also used to steal data
Fansmitter - steal data from air-gapped PCs using sounds emanated by a computer's GPU fan
DiskFiltration - use controlled read/write HDD operations to steal data via sound waves
BitWhisper - exfiltrate data from non-networked computers using heat emanations
Unnamed attack - uses flatbed scanners to relay commands
to malware infested PCs or to exfiltrate data from compromised systems
xLED - use router or switch LEDs to exfiltrate data
Shattered Trust - using backdoored replacement parts to
take over smartphones
aIR-Jumper - use security camera infrared capabilities to
steal data from air-gapped networks
HVACKer - use HVAC systems to control malware on
air-gapped systems
MAGNETO & ODINI - steal data from Faraday
cage-protected systems

0 comments:
Post a Comment